A true human firewall has many responsibilities. The analyst then compares the following results for port 22:
Which Of The Following Best Describes A Human Firewall. The definition of a human firewall is fairly straightforward. It uses global rules applied to users individually. A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future. The average cost of an attack originating from inside an organization is more than that of an outside attack.
 Changes Types: Standard Vs Normal Vs Emergency Change – Bmc Software | Blogs From bmc.com
Changes Types: Standard Vs Normal Vs Emergency Change – Bmc Software | Blogs From bmc.com
Related Post Changes Types: Standard Vs Normal Vs Emergency Change – Bmc Software | Blogs :
A human resources employee sends out a mass email to all. Much like the regular firewall is protecting the network, a team of well trained employees will also protect your business network. Configuring an ids to detect intrusion attempts; What are the three ingredients for an excellent human firewall.
Which of the following would be best to implement in the legacy application?
What are the three ingredients for an excellent human firewall. In cryptanalysis and computer security, ‘pass the hash’ is a hacking technique that allows an attacker to authenticate to a remote server/service by using the underlying ntlm and/or lanman hash of a user’s password, instead of requiring the associated plaintext password as. Implement an ids rule that contains the ip addresses from the advanced persistent threat and patch the routers to protect against the vulnerability. The original firewall configuration can be reset at any time by pressing the reset button. It uses local rules applied to users individually. Furthermore, what best describes a human firewall?
 Source: sec.gov
Source: sec.gov
Implement an ids rule that contains the ip addresses from the advanced persistent threat and patch the routers to protect against the vulnerability. Check the siem to review the correlated logs. And the critical link in that human firewall had received their security awareness training just two weeks earlier.
 Source: buildinghumanfirewall.com
Source: buildinghumanfirewall.com
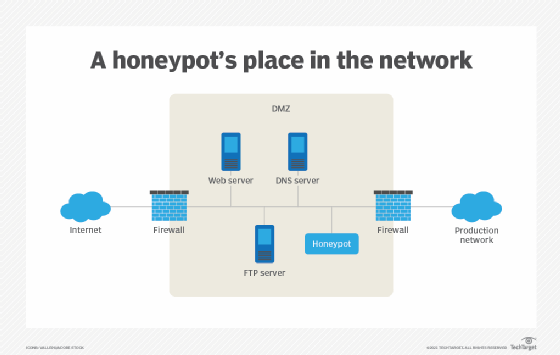
Configure the firewall to allow all ports that are used by this application; Technology that allows information to be shared among small secure groups. It is being used as a honeypot.
 Source: bmc.com
Source: bmc.com
A true human firewall has many responsibilities. These attacks need a human to properly handle them in order to protect your company from loss. A human resources employee sends out a mass email to all employees that contains their personnel records.
 Source: itfreedumps.com
Source: itfreedumps.com
Which of the following best describes the rationale for integration intelligence into hunt operations? The original firewall configuration can be reset at any time by pressing the reset button. Implement an ips rule that contains content for the malware variant and patch the routers to protect against the vulnerability.
 Source: slideplayer.com
Source: slideplayer.com
It uses global rules applied to users individually. Furthermore, what best describes a human firewall? Configure the dlp policies to allow all pii;

You have been asked to enter the following rule into snort: A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future. Maintaining constant vigilance and be aware of threats to our organization.
 Source: slideplayer.com
Source: slideplayer.com
Which of the following best describes the purpose of the tool? It is being used as a windows exploit. Configure the firewall to allow all ports that are used by this application;
 Source: techtarget.com
Source: techtarget.com
A human resources employee sends out a mass email to all. The definition of a human firewall is fairly straightforward. It uses local rules applied to all users equally.
 Source: bootcamp.berkeley.edu
Source: bootcamp.berkeley.edu
A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future. A human resources employee sends out a mass email to all employees that contains their personnel records. A security administrator with full administrative rights on the network is forced to change roles on a quarterly basis with another security administrator.
 Source: chegg.com
Source: chegg.com
It is being used as a honeypot. These attacks need a human to properly handle them in order to protect your company from loss. What are the three ingredients for an excellent human firewall.
 Source: quizlet.com
Source: quizlet.com
The analyst executes the following commands: After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: The firewall costs $65,000 per year to implement and maintain.
 Source: howtodiscuss.com
Source: howtodiscuss.com
The segment should be placed in the existing internal vlan to allow internal traffic only. The average cost of an attack originating from inside an organization is more than that of an outside attack. Portions of a legacy application are being refactored to discontinue the use of dynamic sql.
 Source: quizlet.com
Source: quizlet.com
Much like the regular firewall is protecting the network, a team of well trained employees will also protect your business network. Check the siem to review the correlated logs. Configure the antivirus software to allow the application
 Source: blog.torproject.org
Source: blog.torproject.org
The segment should be placed in the existing internal vlan to allow internal traffic only. Require access to the routers to view current sessions. What people are really meaning when talking about a human firewall is the ability to train employees well enough, that they help secure the network.
 Source: quizlet.com
Source: quizlet.com
It uses local rules applied to all users equally. Which of the following best describes the purpose of an isp? It uses local rules applied to all users equally.
 Source: slideplayer.com
Source: slideplayer.com
Furthermore, what best describes a human firewall? The segment should be placed on a separate vlan, and the firewall rules should be configured to allow external traffic. In cryptanalysis and computer security, ‘pass the hash’ is a hacking technique that allows an attacker to authenticate to a remote server/service by using the underlying ntlm and/or lanman hash of a user’s password, instead of requiring the associated plaintext password as.
 Source: slideshare.net
Source: slideshare.net
Configuring an ids to detect intrusion attempts; Out of the firehose of rsa data, i distilled the 7 urgent reasons why you need to create your human firewall as soon as you possibly can. These attacks need a human to properly handle them in order to protect your company from loss.
 Source: quizlet.com
Source: quizlet.com
In cryptanalysis and computer security, ‘pass the hash’ is a hacking technique that allows an attacker to authenticate to a remote server/service by using the underlying ntlm and/or lanman hash of a user’s password, instead of requiring the associated plaintext password as. What is a human firewall? Use a packet analyzer to investigate the netflow traffic.
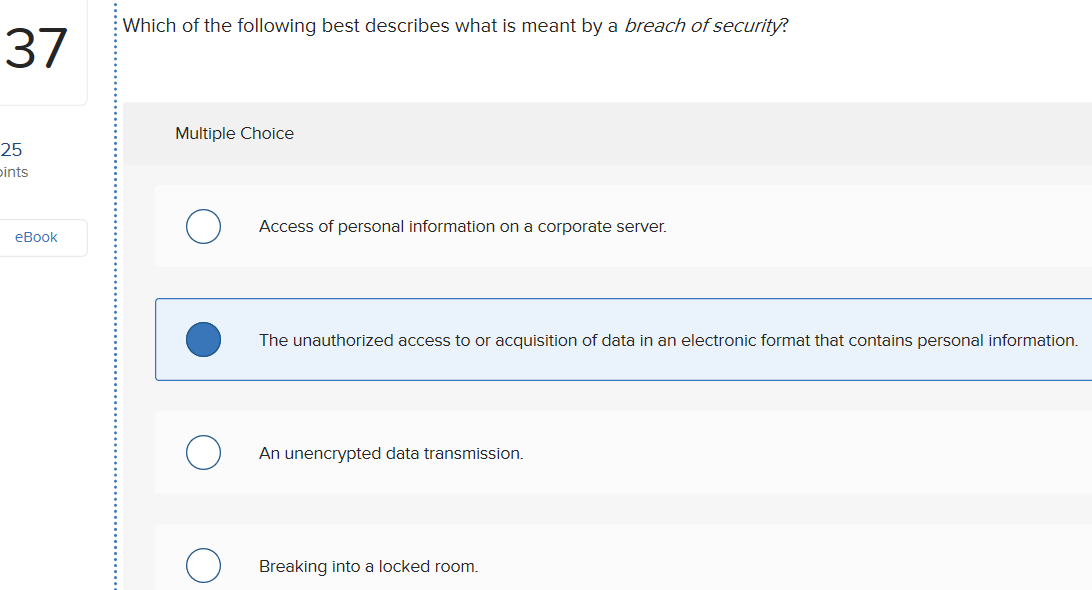 Source: chegg.com
Source: chegg.com
Configuring an ids to detect intrusion attempts; What type of app are you likely using? It uses local rules applied to users individually.
 Source: blog.knowbe4.com
Source: blog.knowbe4.com
Portions of a legacy application are being refactored to discontinue the use of dynamic sql. A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewall’s behavior and responses. Configure the dlp policies to allow all pii;
Also Read :